Background
Following a high-profile third-party breach, a major UK public sector organisation turned to Resillion for a 3-month Red Team exercise.
The number one fear was having an attacker successfully gain control of their Pension Officers IT account and being able to access their multi million pound pension fund.
This was their first Red Team engagement, a bold step toward embedding a security-first culture and validating their newly implemented policies and technical controls.
This initiative was to infiltrate their pension fund officer’s protection of the pension along rigorously test the organisation’s cyber resilience across people, processes, and technology.

Key Challenges
Third-Party Sensitivities
Testing their systems posed a diplomatic challenge. Given their history of breaches, they were understandably hesitant to participate.
Strong Technical Defences
The organisation had already deployed robust security measures, including conditional access policies and privileged identity management. These defences required the Red Team to develop creative, non-standard attack strategies.
Policy vs. Practice
Despite having sound policies in place, execution gaps were evident. For instance,clear-text passwords were found in accessible SharePoint files, and weak passwords were used to protect sensitive documents.
Human Vulnerabilities
Employees were susceptible to novel attack vectors, such as spear-phishing via Microsoft Teams, highlighting a need for more nuanced user awareness training.
Approach & Solutions
Advanced Phishing Tactics
The team used spear-phishing emails with defence evasion techniques that bypassed Microsoft SafeLinks. This led to successful account compromises and exposed weaknesses in user defences.
Credential Exploitation
With compromised credentials, tools like Graph Runner were used to enumerate and exploit sensitive data stored insecurely in SharePoint and other repositories.
Transparent Communication
Weekly updates kept the organisation informed without prematurely altering the environment. This ensured trust and control throughout the engagement.
Awareness Workshops
Post-engagement sessions focused on unconventional attack methods like phishing via trusted platforms to help staff better recognise and respond to emerging threats.
Key Metrics
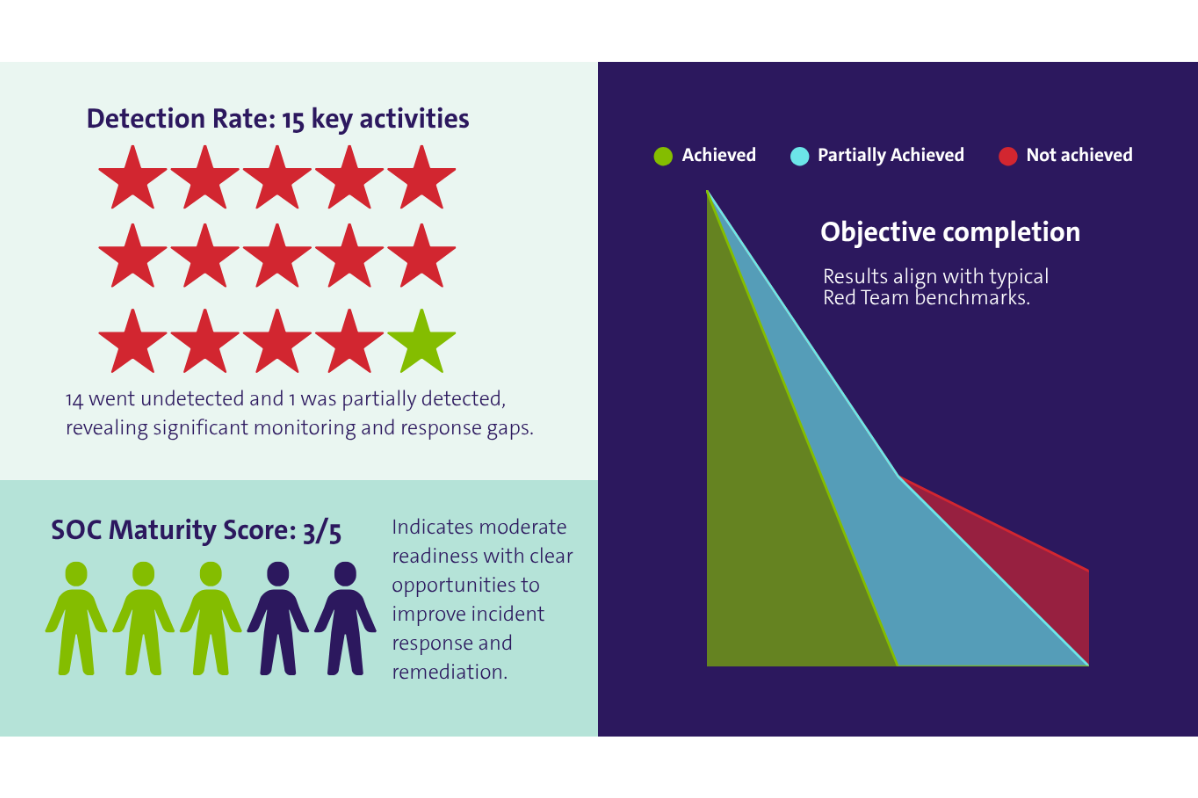
Critical Findings
Credential Management Flaws:
The discovery of clear-text passwords in shared locations pointed to systemic issues in how credentials were stored and protected.
The human error factor:
Despite strong technical controls, the Red Team ultimately gained access to the well-guarded pension fund following a prolonged targeted attack. This incident underscored the reality that even the most secure systems can be compromised through behavioural vulnerabilities.
We managed take control through the Pension Officer’s actual email. Our client in including the Pension Officer was shocked and realised that their worst fear came true.
Outcomes & Reflections
Overall, getting access to the pension fund was not easy for the Resillion team. The gatekeeper for the Officer was security conscious, and our clients security defences proved effective in most cases however our focused persistent efforts resulted in the infiltration and subsequent control of the Officers email address.
While the Red Team did succeed in breaching the pension fund, the Resillion team came away impressed by the overall maturity of the security posture. The breach was not due to a lack of controls, but rather a reminder that human factors remain the most unpredictable element in cyber security.
The engagement’s findings helped the organisation secure funding for future cyber security initiatives to improve detection and response capabilities iteratively.
Our Accreditations and Certifications







